The days of handwritten assignments, printed textbooks and paper reports have already passed; In the 21st century, learning is digital . Students usually do homework, communicate with classmates, check their grades and research through the Internet.
Internet streamlines students' ability to study and connects them instantly with more information than a whole school library could contain. However, the digital world of modern education can be dangerous both for your students and for you as a teacher.
Your risks as a teacher
Your students handle computer science better than you could imagine. While many adults rely on the occasional tutorial on how to use an application or a new program, students are native to the digital age; They intuitively know how to use applications, mobile devices and online platforms since they have been using them all their lives.
This means that, with the right motivation, your students could learn to hack your accounts . For example, if a student was not satisfied with her grade, she could find out your password and change a couple of notes. Similarly, a student who would like to play a joke on you could change all the images in your PowerPoint presentation.
You need to know how to protect both your students and you from cyber attacks.
Cyber security for students
In some cases, a student of yours may be responsible for cyber security problems in your class, but in others it could be the victim.
Although many young people are able to learn to use programs easily and may even know some hacking, they still have a lot to learn about life. They may not be able to discern all the cyber-security risks with which they are.
As a teacher, you can directly protect your students and teach them about cyber-security so they can protect themselves better.
Protecting your class
Cyber-security threats can be alarming, but, fortunately, there is a simple solution to keep you and your students safe: education! After all, knowledge is power.
By training and training your students in cyber-security, the latest applications and other elements of modern technology, you can discover and solve digital security issues before they endanger your class .
How students put you in danger
Even unintentionally, your students could put you, the school and their peers in danger with their digital habits. In this section we will describe these hazards and explain how to avoid them.
Integrating the Internet in your class
As we said above, your students tend to know more about computers than you do . They probably know how to use absolutely all of the most popular digital programs and devices, which could give them a huge advantage over you if they wanted to hack your accounts .
Your first instinct could be to totally ban digital devices in your classes . However, that is unlikely to work; According to the Pew Research Center , in 2018, "95% of teenagers have access to a smartphone and 45% say they use it" almost all the time. "»
This means that your ability to eliminate the use of phones, tablets and laptops during class is very limited, and fighting the use of digital devices in your class is probably futile and frustrating. Instead, make the time your connected students spend a productive part of the class by integrating your students' devices into your lessons (for more information, read our lesson plans ).
Who uses your user accounts?
As a teacher you probably have many accounts; In addition to your personal email and social network accounts, you will also have multiple educational and center software accounts.
Imagine that your students had access to all the information stored in those accounts: they could read your personal emails and social media accounts, change their tasks and notes, see the reports of other students, publish false updates in your profiles or hack you from many other forms.
Hacking your accounts is probably not very difficult for your students, and to make matters worse, many schools do not have good cyber-security systems in place to help you protect your accounts .
To protect your important information from potential hackers, it is essential to understand how to protect and secure your accounts.
Below we offer you our suggestions on how to keep your user accounts safe , and the information is relevant to your online teacher portals, personal accounts, emails and social networks. We recommend you:
- Use the center's email address to create accounts that have to do with teaching. This will keep your personal email out of accounts that students could access.
- Create complex passwords Your passwords should be a combination of uppercase and lowercase and include numbers and symbols. This type of password is very difficult to find out.
- Change your passwords frequently. Experts recommend changing passwords every six months, but since that is almost the entire duration of the school year, we recommend changing them every three months .
- Use a different password for each account. For example, the password you use for your teacher portal should not be the same as that of your personal Facebook; That way, if someone finds out or hacks a password, they will not be able to access all of your accounts.
- Check if your password is strong enough using a tool like ours . This type of tool calculates the difficulty of finding out or hacking your password.
- Use a password manager to generate and store your passwords on your device or browser. A password manager uses a special database to create and store strong passwords so you do not have to remember them.
- Use bio-metric passwords whenever you can, such as access through the fingerprint. It is very safe and only you can access.
- Take advantage of two factor authentication whenever you can. These systems require that you enter your password and a special code that is sent to your phone or email. Strong authentication offers the best protection for sensitive accounts such as your email address or bank account. Many services offer this authentication optionally. Discuss the matter with your service provider if you are not sure how to start.
This should help you keep your accounts safe from students and other potential hackers.
Improving mobile security
Probably depend on your smartphone to be in contact with friends, check your email and post on social networks. You can even use a mobile device to assign and correct tasks or find information for your class.
Smartphones are incredibly useful and convenient, but they are also very vulnerable to being hacked by your students.
Your smartphone may be expensive, but the data you store there is probably more valuable. Photos, social network accounts, personal messages, bank accounts and all kinds of private information are stored today in mobile phones .
If you do not take the proper precautions, a student, a former member of the faculty or a stranger could access the data on your smartphone or tablet. There are four ways to protect your mobile devices from potential hackers:
- Keeping your devices updated. The hackers look for errors in the systems of security of the companies, and they are almost as fast as the companies at the time of trying to stop them removing software updates. No system is 100% secure, but updating your software is one of the best ways to protect your phone; we recommend you enable automatic updating on all your applications and devices.
- Using bio-metric passwords As mentioned above, bio-metric passwords are one of the most secure login options for your digital devices. Keep your smartphone and tablet safe by establishing fingerprint passwords whenever possible. At a minimum, use a traditional password to access your mobile device.
- Disable Wi-Fi and Bluetooth whenever possible. Wi-fi and Bluetooth are great when you use your device, but when not, leave the wi-fi and Bluetooth enabled informs hackers that you're there. We recommend deactivating them when you are not using your device since it will limit your visibility in nearby devices.
- Customize the encryption settings. The settings that come by default in your device and its applications may not be ideal in terms of cyber-security; If your device does not have encryption enabled by default, enable it. You should also modify your privacy settings to limit the access of different applications to your data.
These security measures can help keep your mobile devices safe from students and can also protect you from other potential hackers wherever you go with your smartphone or tablet.
Maintaining your personal privacy and maintaining an impeccable reputation on the Internet
You probably do not talk about your romantic relationships, political opinions or favorite celebrities with your students. However, if you do not properly protect your social media accounts , your students could easily access all that information.
Most teachers would prefer to keep their personal lives and social media accounts private and well away from their students, and for good reason. According to an article in Inc . magazine , "privacy matters more to the Z generation, a generation of people who care a lot about the management of their reputation on the Internet." As students worry a lot about their reputation on the Internet, they are also very aware of yours .
Like your teacher, you have to be careful of what your students discover about you on the Internet . If they find out about your recent break-up on the Internet, see photos of you at a concert or find out what you think about a controversial topic, they may be less comfortable in your class or question your authority. It is important that you remain a respected and trusted figure in their lives .
Most teachers are tempted to erase all their information from the Internet, but you do not have to go to that extreme. After all, you should still be able to use the Internet to connect with your friends, express yourself, post photos and more.
To keep your personal information safe from your students (and anyone you do not trust), you have to hide your online presence in an intelligent way .
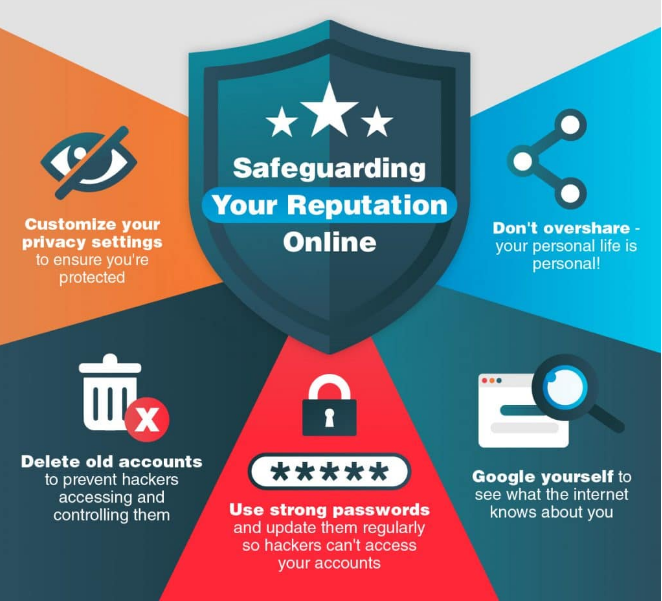
Our experts recommend the following steps to protect your reputation on the Internet:
- Find yourself on Google. If you can find yourself in a search engine, your students can also. Searching yourself on Google will reveal almost any personal information that is publicly available. Once you know what information about you is on the network, you can find its source and erase everything you would not want your students (or anyone else) to see
- Modify your privacy settings. Many accounts come by default with minimal privacy settings. If you want your personal information to be far from your students, make sure your posts, tweets and other social networks are private and only visible to your friends or followers; this way your students will not be able to find this information easily.
- Remove and / or deactivate accounts that you do not use. If you have an old social network account that you no longer use, you should delete or deactivate it; this way you will avoid that no impostor can get access to the account and publish in your name. If you want to keep your old accounts, make sure you at least make them private.
These guidelines will help you enjoy social networks and protect your reputation on the Internet at the same time.
Internet in your class
Your students and you will be connected in the center , so it is essential that you know how to be protected and how to protect them. Next, we explain how to do it.
Is the network of your educational center safe?
The network of your educational center is probably the main way your students and you access the Internet. It can also be a way to block certain unsafe or inappropriate websites and improve the cyber-security of your center. Unfortunately, it could also be vulnerable to gaps that could put them at risk.
Students can overcome the network and access blocked websites in many ways. As our article on this topic informs , students can use a VPN, a proxy or a special browser to overcome the measures of the educational network. These tools could help you unlock certain websites and access inappropriate content in your class, which could be dangerous and disruptive.
Now that you are aware of how students can overcome the blockages of the center's network, you can work with technology professionals to prevent them from doing so. You can also be aware if you discover that your students see inappropriate content in class.
Also, if your school's network is not password protected, it could be even less secure. Hackers often enter public Wi-Fi networks in search of personal data of users and try to take control of their devices. This could leave you, your students and administrators vulnerable to malicious attacks.
In fact, in September 2018, the FBI issued a public statement warning about the growing cyber-security risks that schools face. The FBI said the collection of sensitive information in schools "could present unique opportunities for offenders" and could lead to "social engineering, bullying, tracking, identity theft or other attacks on young people."
There is no doubt that you and your students face cyber-security risks if the educational network is not insured. If it's an open network, you can work with administrators and IT professionals to make it more secure.
We recommend adding a password to your school's Wi-Fi and changing it every three months. It could also be useful for the center to hire a cyber-security professional who establishes advanced anti-hacking systems .
The dangers of cyber-bullying
According to the NGO Kids Health , "cyber-bullying is the use of technology to harass, threaten or embarrass another person."
The organization explains that "sometimes it can be easy to discover cyber-bullying", such as seeing "a text message, a tweet or a cruel or rude response to a Facebook status." However, Kids Health states that "other acts they are less obvious, such as impersonation of a victim on the Internet or publishing personal information, photographs or videos designed to embarrass another person. "
Unfortunately, cyber-bullying is very common in many schools . A 2018 poll by the Pew Research Center found that 59% of American teens have been harassed online. The study found that 90% of young people believe that online bullying is a problem that affects people their age.
The same study found that "the majority of young people think that teachers, social network or political companies are not doing everything necessary to face this problem".
As you will suppose, cyber-bullying can have a devastating long-term effect on children and adolescents . Like other forms of bullying, it can lead to consequences that will affect the victim throughout his life, young people can suffer depression, anxiety and have low self-esteem as a result of bullying .
They may also want to avoid going to class , which affects your ability to teach them the values and teachings necessary to succeed in the adult world.
As a teacher, you may be an observer of cyber-bullying without realizing it . It can be difficult to identify bullying and know what is the best way to intervene when it is happening in a platform or online messaging service to which you do not have access; However, as you need to protect students from their effects, it is essential to know how to identify bullying in your class .
The vocabulary of cyber-bullying
If you want to protect the students in your class from bullying, you have to be familiar with some terms. These include:
- Trolling (known as "trolling" in Spanish): posting provocative or insulting messages intentionally, for example, of racist or sexist content, to encourage response. Merriam-Webster defines the verb "trolling" as "antagonizing others on the Internet by deliberately publishing provocative, irrelevant or offensive comments or other disruptive content."
- Flaming: send provocative messages to incite a discussion. According to Lifewire , "flaming consists of insulting, offending or any other type of verbal hostility directed at a particular person."
- Harassment: perform actions specifically directed at a person or group in order to annoy or annoy. Harassment can become stalking, a familiar term that means spying on another person.
- Stalking: According to the Cyber-bullying Research Center , "cyber-stalking involves using technology (Internet!) To make someone worry about their safety. Cyber-stalking includes getting hold of someone's personal and private information to scare them, sending messages hundreds of times a day to let them know that you are spying on them, spying on their social networks to find out where they are and being able to appear without being invited, or publishing about the person continuously. and without his permission. "In many places, cyber-stalking goes against the law.
- Cat-fishing: stealing someone's Internet profile or creating false profiles to start online relationships. This form of cyber-bullying can also be used to spy on, shame or manipulate children, adolescents and even adults.
- Fraping: Impersonate another person or enter their profile to post inappropriate content. This constitutes a serious offense and, according to Business Insider , "now it is a crime that in Ireland could be punished with 10 years in prison."
- Griefing: abuse and make others angry in online games. According to Oxford Dictionaries, a "griefer" is "a person who deliberately harasses or provokes other players or members [of a community of an online game] to ruin their fun."
- Outing: publicly share information, photographs or personal, private or embarrassing videos of another person. This can be very harmful especially among children and adolescents, who may not react in a compassionate way.
- Roasting: when an individual or, usually, a group harasses a person on the Internet until the victim "falls apart". The blog Bark explains that "roasting is a term in the world of comedy that consists of a humorist making humorous jokes about another person", but becomes problematic when it is done "without the consent or desire of the victim". Although "it can start being harmless and nothing serious ... it does not always end there."
If you see your students talking about these types of activities, you should pay attention; Talking about cyber-bullying with your students could help you avoid suffering their dangers .
How to know if a student is being a victim of cyber-bullying
Even if you do not hear your students talking about cyber-bullying, you may be able to discover a student who is being victimized by this type of attack. Children and adolescents who are bullied often show signs of bullying and anguish .
A student may have been harassed if:
- Usually seen alone or alone. Harassed children can get away from their peers or feel that they can not trust anyone.
- Change your group of friends suddenly. Sometimes, the authors of the harassment are the same friends of the students. In these cases, the student may no longer want to spend time with the old friends who harassed him.
- He suffers from sudden changes in his personality. These could include looking anxious, sad or angry or isolated.
- He cries habitually, sometimes or in circumstances that seem strange. A student may feel upset in seemingly strange circumstances when he is suffering the consequences of cyber-bullying. It could happen when other students laugh at the victim or remind him of what happened on the Internet.
- It starts to get worse grades. The academic performance of harassed students can get worse when they feel upset, scared or unable to concentrate.
- He seems distracted or lacks concentration in class. Students who have experienced cyber-bullying may be worried because of their fear or shame rather than focusing on the class.
- Usually miss class. Students who have been harassed by their peers may want to avoid going to class so they do not have to deal with their stalkers.
- Loses interest in extracurricular activities. Children and adolescents victims of cyber-bullying may want to leave their athletic teams, dance or theater groups or other activities to get away from their stalkers. They may also be less interested in extracurricular activities because they feel embarrassed, shy, or fear that they will be hurt again.
- He suffers from an increasingly lower self-esteem. Children and adolescents victims of cyber-bullying often lose confidence because they could believe the negative things that their stalkers say about them.
- It does not look as good physically. The mental and emotional stress of cyber-bullying could worsen the health of the victims.
If these descriptions make "light bulb turn on", you should have a conversation with your students about cyber-bullying. The sooner you can intervene and stop this harmful behavior, the better.
























![How to Create a New Bluehost Account [Avoid This Common Mistake]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgUJaXUuCx3zxPOPe9dNo65lLKNDr949kTri74T9x-mMwC6UwIgIqkiRY0Z9gDb08QxGbQmD1o8IGwWML_tBjbMpRtosxgMVBKKoZKcJn9Iay6FEh2YgjcdNDU1AiO6KhxE3yyhDh-dVcI_/w72-h72-p-k-no-nu/Capture.PNG)
